User provisioning (via SCIM)
SCIM
System for Cross-domain Identity Management (SCIM protocol) allows the integration between an Identity provider and other applications
User provisioning
The LYNKS application supports user provisioning using the SCIM protocol, enabling the management of users and access and permissions directly from the centralized Identity Provider of our clients.
User provisioning allows organizations to manage their users centrally by integrating their external user directory directly with the LYNKS application. This integration allows to automatically update the users and groups in LYNKS when making updates in your identity provider.
Role and permission based access control
Employees require different access levels based on their role or department in the organization. User provisioning makes it possible to allocate granular role-based access controls while giving an organization the ability to customize access based on internal policies and regulations.
Creating groups, organizations can classify users by their role and expected permissions, which will then reflect on the application.
On LYNKS, users provisioned from the external IdP will be marked as follows:
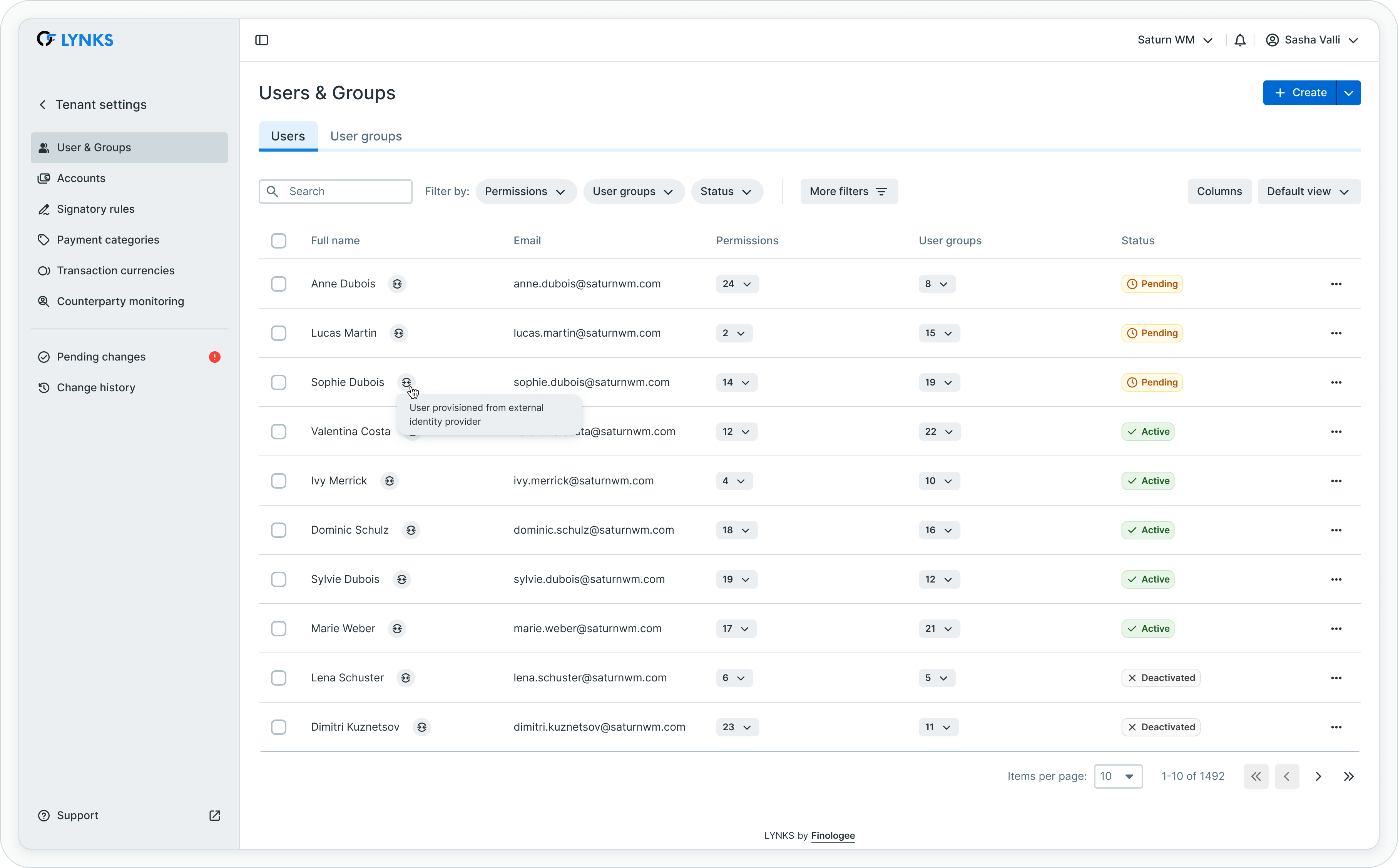
Some user management actions will be restricted for provisioned users, like for example updating their membership to a group or changing the personal details, as these parameters are defined by the IdP.
Access and permissions can be managed either through the SCIM protocol, by adding/removing users to user groups, or directly per user/ user group.
Different Identity providers
List of supported Identity providers:
- Azure AD / Entra AD
- Okta
Note: user groups must be the same in the SCIM configuration as in the Identity Provider
Updated 2 months ago
