Payment approvals
Understanding how signatory rules establish payment authorization workflows based on risk parameters and organizational policies
Introduction
Payment approvals in LYNKS ensure that every payment receives appropriate authorization before submission to the bank. This approval mechanism is governed by signatory rules—configurations that define which payments require authorization and who can provide it based on transaction parameters.
The payment approval concept separates payment creation from payment authorization. Users who create payments may not have authority to approve them, while approvers review and authorize payments created by others. This separation enforces the maker-checker principle, reducing fraud risk and preventing erroneous transactions from reaching the banking system.
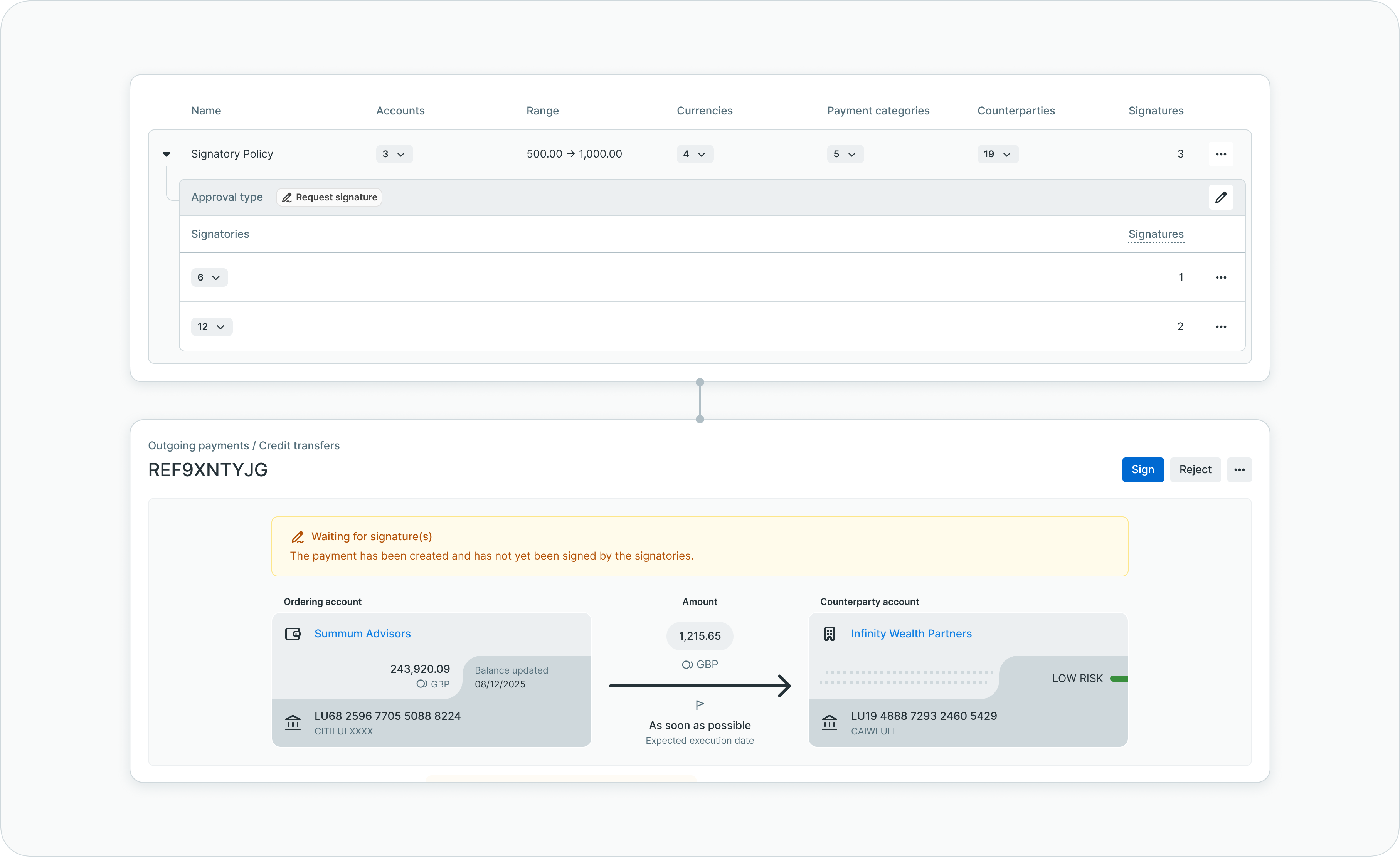
The signatory rule concept
Signatory rules form the foundation of payment approvals in LYNKS. Each rule defines a set of conditions that determine when it applies to a payment and specifies the authorization requirements for matching payments.
Rule matching logic
When a user creates a payment, LYNKS evaluates the payment's characteristics against all configured signatory rules. These characteristics include the payment amount, the account from which funds are debited, the currency of the transaction, the payment category, and potentially the counterparty receiving the payment.
A signatory rule applies to a payment when all of the rule's parameters match the payment's characteristics. For example, a rule specifying EUR transactions from Account A between €1,000 and €10,000 applies only to payments meeting all these criteria simultaneously.
How signatory rules match payment parameters
Authorization specification
Once a signatory rule matches a payment, that rule determines the authorization requirements. The rule specifies which users or user groups can approve the payment, how many approvals are required, and whether the payment undergoes manual review or automatic processing.
This specification creates a direct link between payment risk characteristics and authorization requirements. Higher-value payments can require more approvals, certain payment categories can mandate specific approvers, and low-risk transactions can be automatically approved.
The approval workflow
Payment approval follows a structured workflow from creation through authorization to bank submission.
Workflow stages
Creation and validation: When a user creates a payment, LYNKS immediately validates whether any signatory rule covers the payment parameters. If no rule matches, the payment cannot be created—this represents a gap in the signatory matrix. If one or more rules match, the payment enters the approval workflow with those rules defining the requirements.
Approval collection: The payment moves to pending authorization status. Eligible approvers—as defined by the matching signatory rule(s)—receive notifications. These approvers review the payment details and either authorize or reject the payment. The system tracks which approvers have acted and how many approvals remain needed.
Completion and submission: Once the required number of approvals is collected, the payment becomes ready for bank submission. LYNKS transmits the payment to the bank through the configured connectivity channel. The payment then follows the bank's processing workflow.
Approval methods
Signatory rules can specify three distinct approval methods:
Manual approval requires designated users to explicitly review and authorize the payment. This method provides human oversight and judgment for transactions requiring scrutiny. Manual approval supports multi-level authorization where multiple approvers from different groups must independently authorize the payment.
Auto-approval automatically authorizes matching payments without human intervention. This method suits low-risk transactions or scenarios where the payment creation itself constitutes sufficient authorization. Auto-approval reduces operational overhead while maintaining audit trail records.
Auto-rejection automatically rejects matching payments, preventing their submission to the bank. This method blocks prohibited transaction types or enforces compliance restrictions. Auto-rejection rules make policy enforcement explicit and automatic.
Overlaps and gaps
The interaction between multiple signatory rules creates two important concepts: overlaps and gaps.
Overlaps
An overlap occurs when multiple signatory rules simultaneously match a payment's parameters. In this scenario, the payment must satisfy the authorization requirements of all matching rules. If Rule A requires two approvals and Rule B requires one approval, a payment matching both rules requires three approvals total.
Overlaps can be intentional—providing additional security layers for sensitive transactions—or unintentional side effects of rule configuration. Organizations must understand their overlap landscape to ensure approval requirements align with intended policies.
Gaps
A gap represents a combination of payment parameters not covered by any signatory rule. Since every payment must match at least one rule to proceed, gaps effectively block certain payment types from being created.
Organizations can use gaps strategically to prevent unwanted transactions, but unintentional gaps can disrupt legitimate operations. The gap concept helps administrators identify incomplete coverage in their signatory matrix.
Governance and compliance
Payment approvals serve multiple governance and compliance objectives beyond basic authorization.
Segregation of duties
The separation between payment creators and approvers enforces segregation of duties—a fundamental internal control principle. This separation ensures that no single individual can both initiate and authorize a transaction, reducing fraud opportunities and error propagation.
Different signatory rules can require different approvers based on transaction characteristics. High-value payments might require senior management approval, while routine payments need only operational-level authorization. This tiered authorization matches approval authority to transaction risk.
Audit trail
Every step in the payment approval workflow generates audit records. These records document who created the payment, which signatory rule(s) matched, who provided approvals and when, and the final disposition (approved, rejected, or cancelled).
This comprehensive audit trail supports compliance requirements, internal investigations, and operational analysis. Organizations can trace payment authorization decisions and identify patterns or anomalies in approval activity.
Risk management
Signatory rules function as a risk management tool by making approval requirements proportional to transaction risk. Amount thresholds ensure that higher-value payments receive greater scrutiny. Payment category restrictions can enforce operational policies or compliance requirements. Counterparty-based rules can address relationship-specific risks.
Related documentation
Explore related sections for more information:
- Signatory Rules - Approval workflow configuration - Detailed configuration and usage instructions
- Tenant Settings Approvals - Configuration change approvals - Configuration change approvals
- Permissions - Comprehensive explanation of access control and role-based permissions - Permission management
Support
For questions about payment approval concepts or signatory rule strategy, contact [email protected].
Updated 3 months ago
